Malware Traffic Analysis Exercise (StingrayAhoy)
20-04-2019
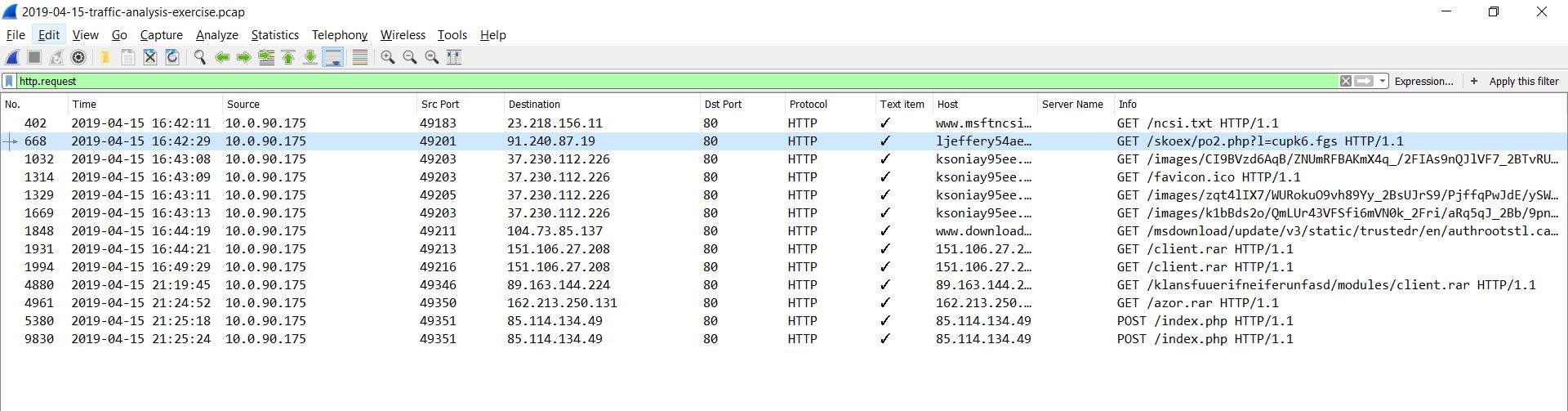
I got this malware traffic exercise from malware-traffic-analysis.net. I opened the file in wireshark and applied the “http.request” filter.
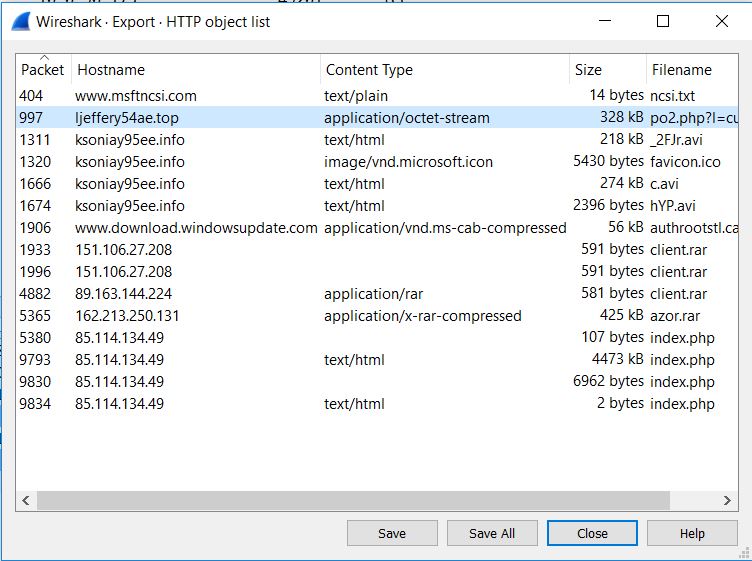
Let’s export the http objects and analyse them.
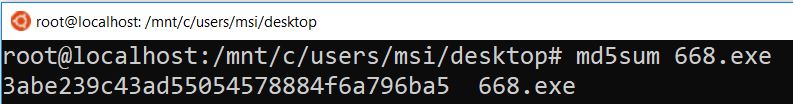
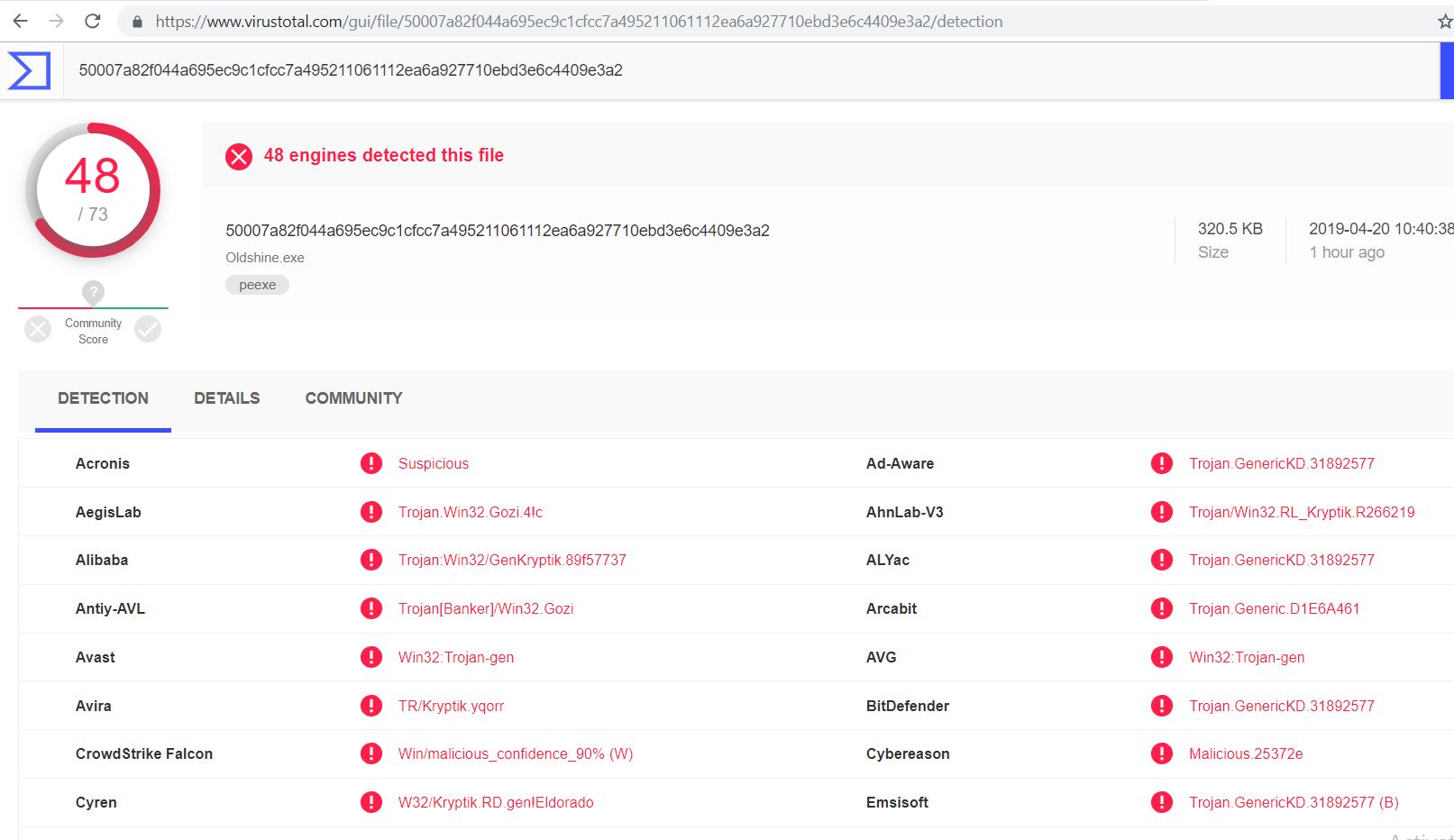
Second http object pointing to hostname ljeffery54ae.top seems red flag to me. I uploaded the hash to virustotal.com and yes it’s a malware.
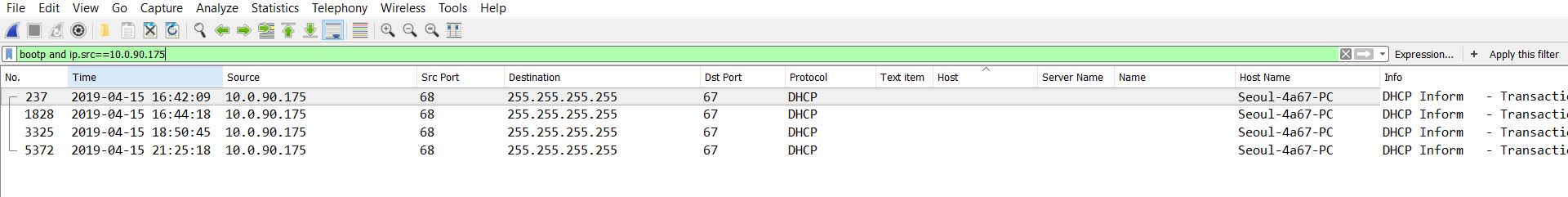
Now, let’s see who is infected with this malware and what does it do. I see PC with IP “10.0.90.175” downloaded the malware and then I applied filter “bootp and ip.src==10.0.90.175” and got the following results :
So the host name is “Seoul-4a67-PC”.